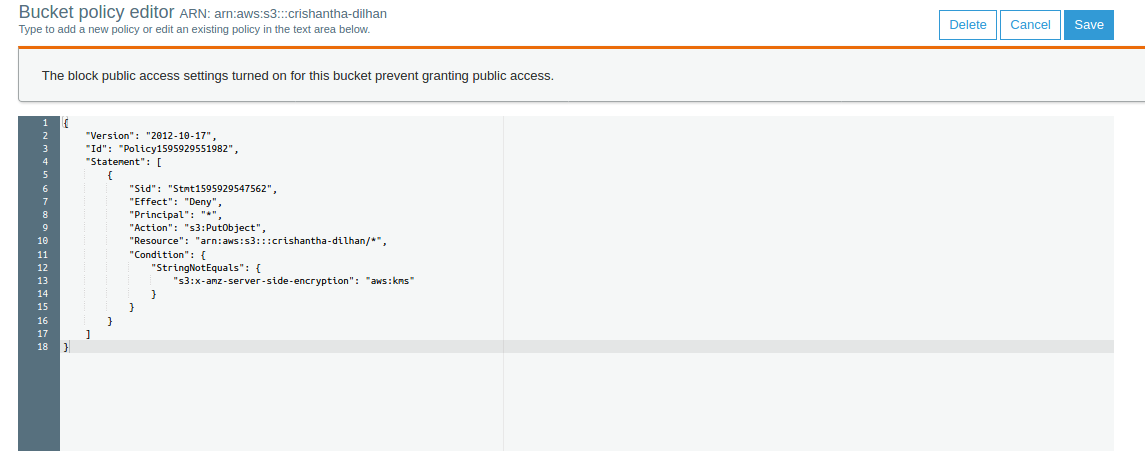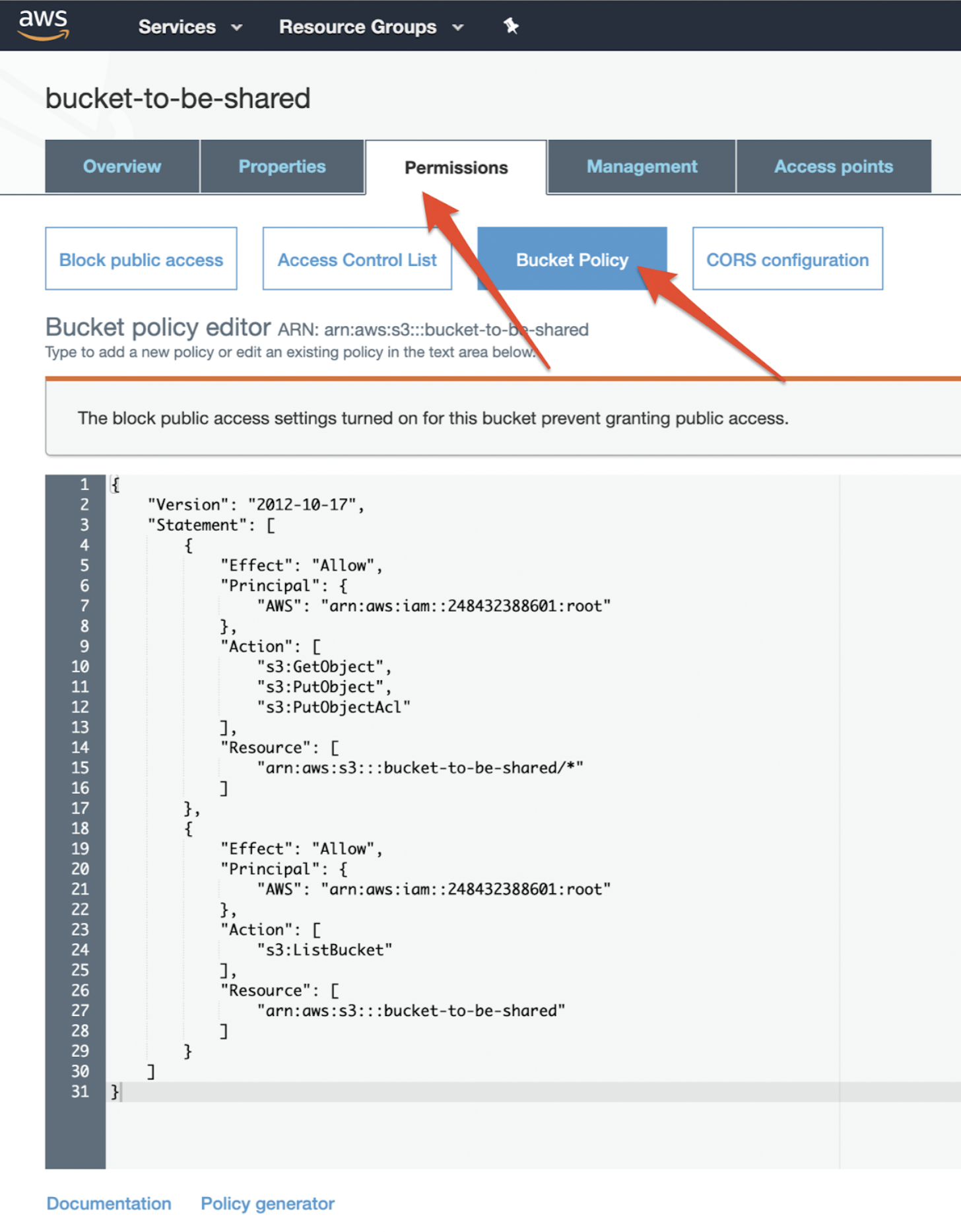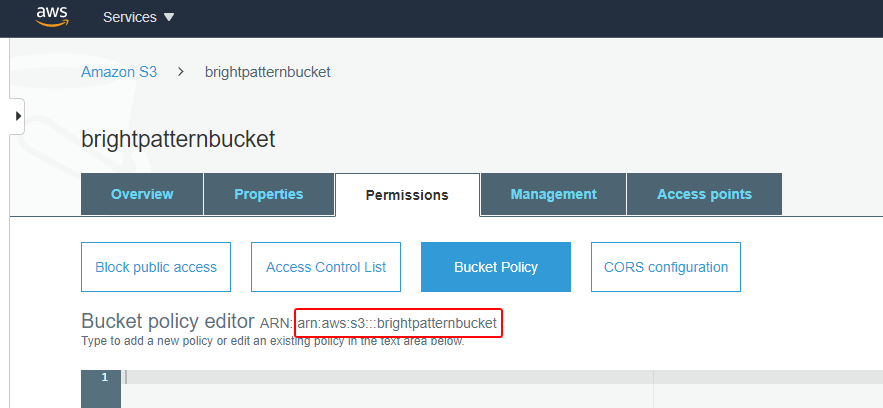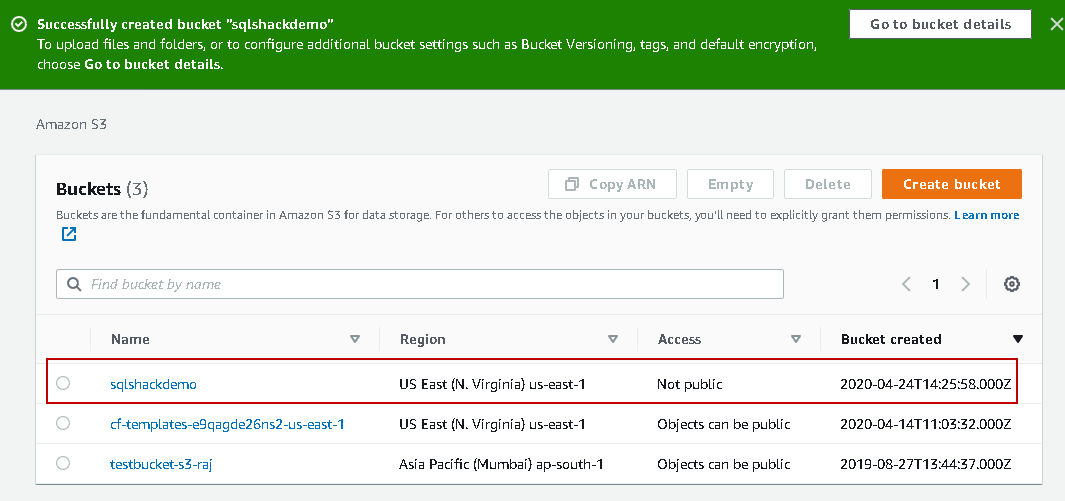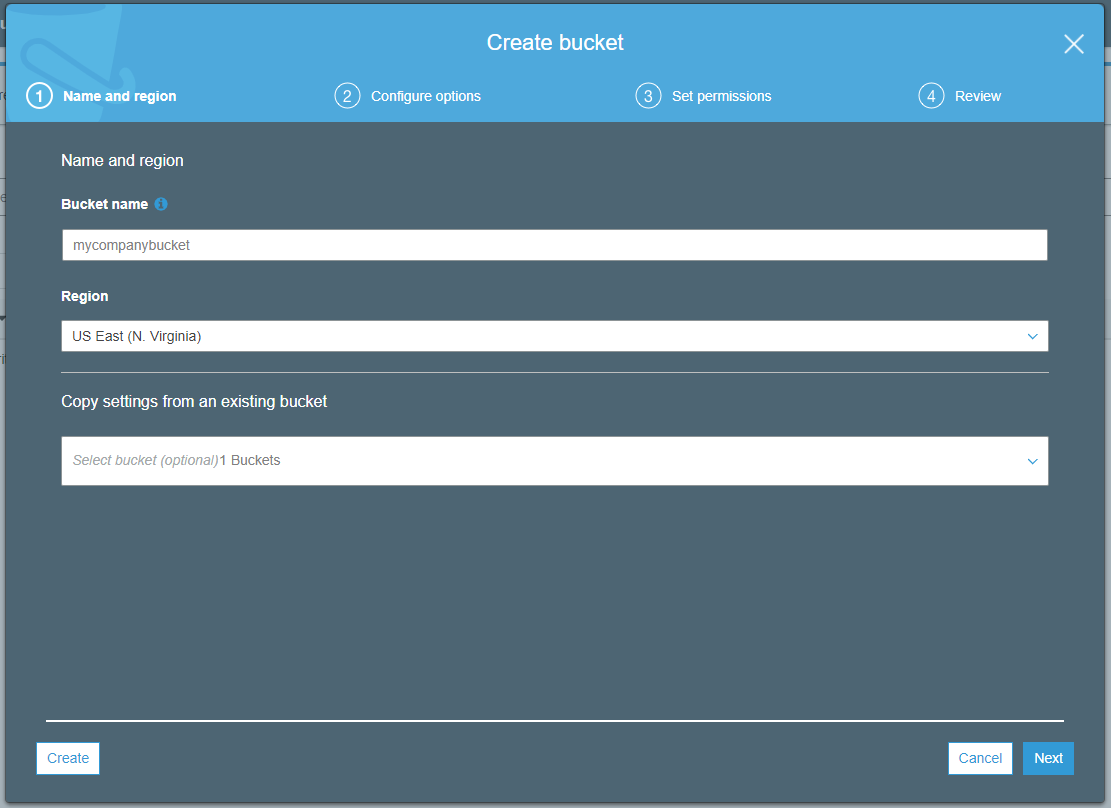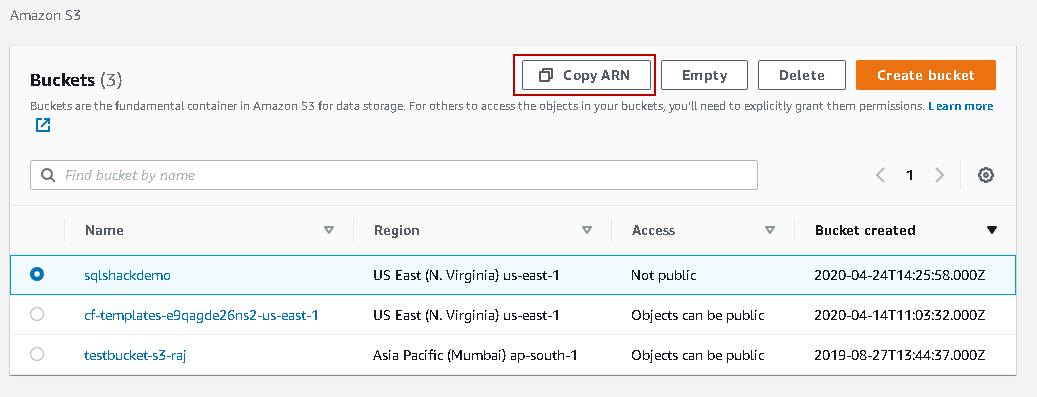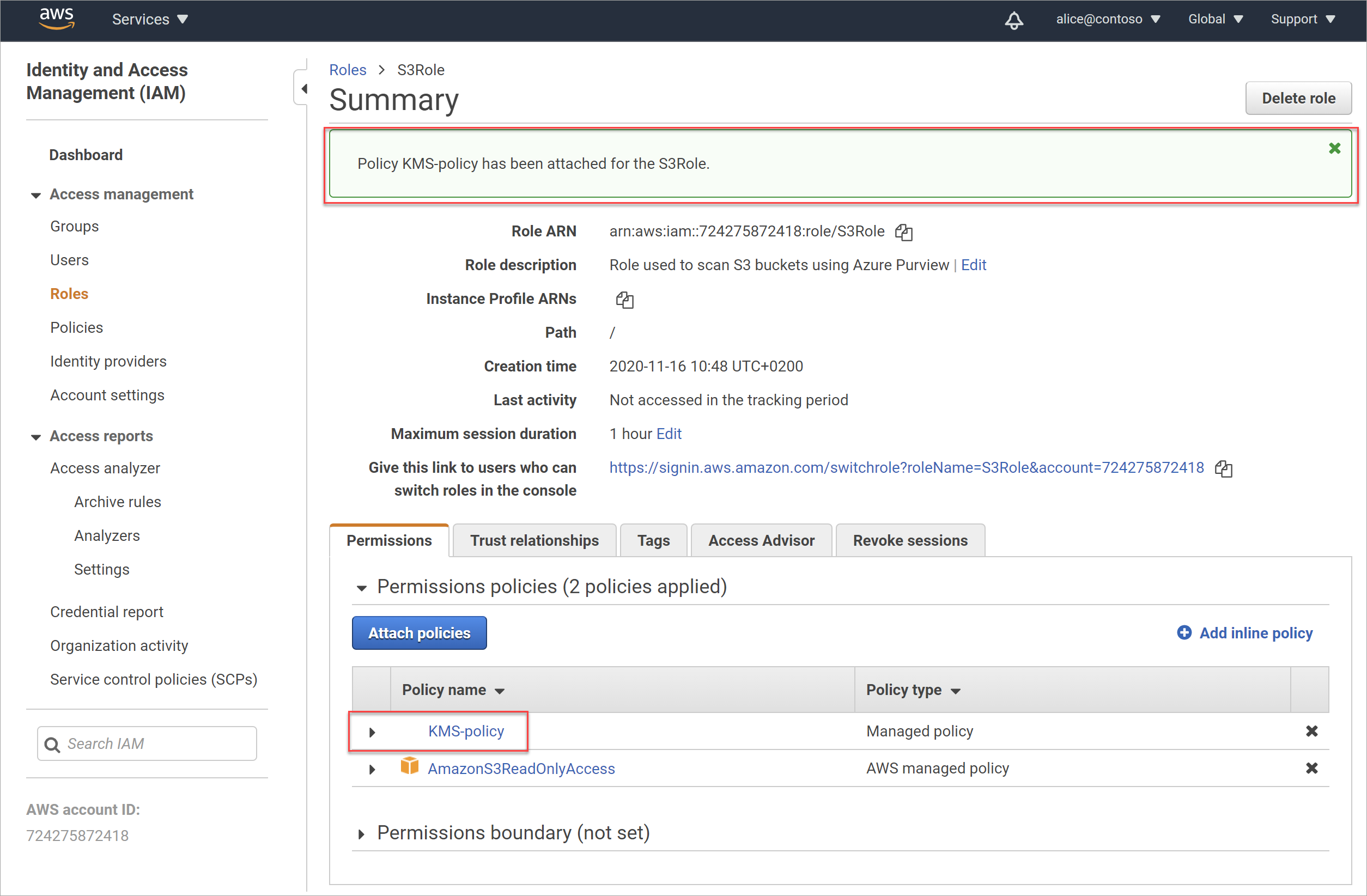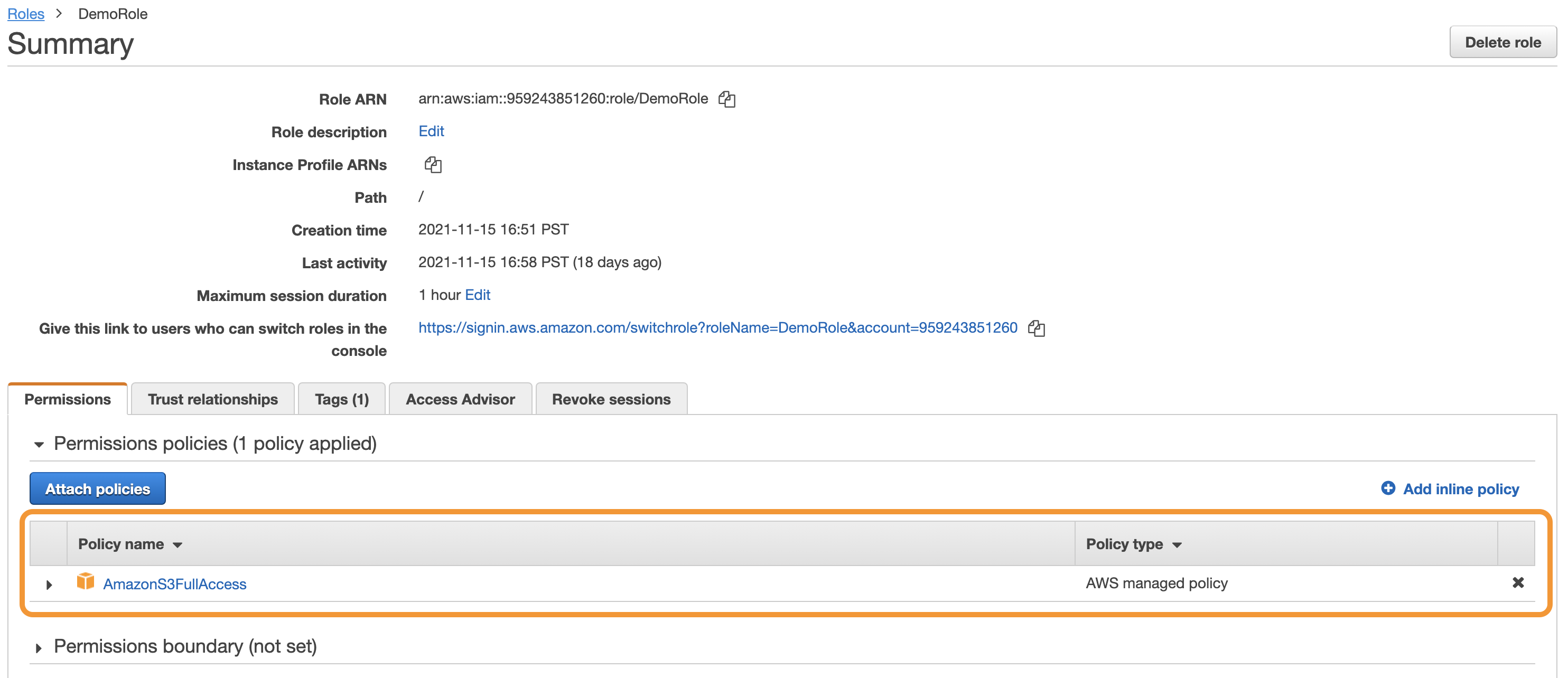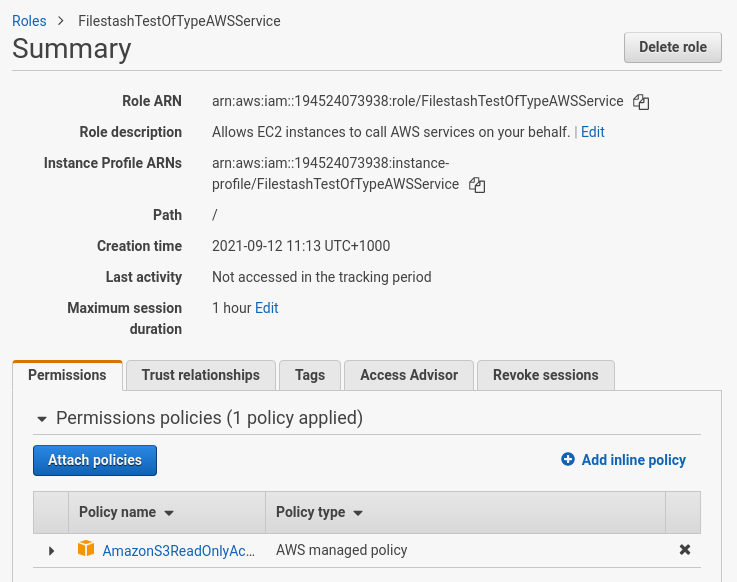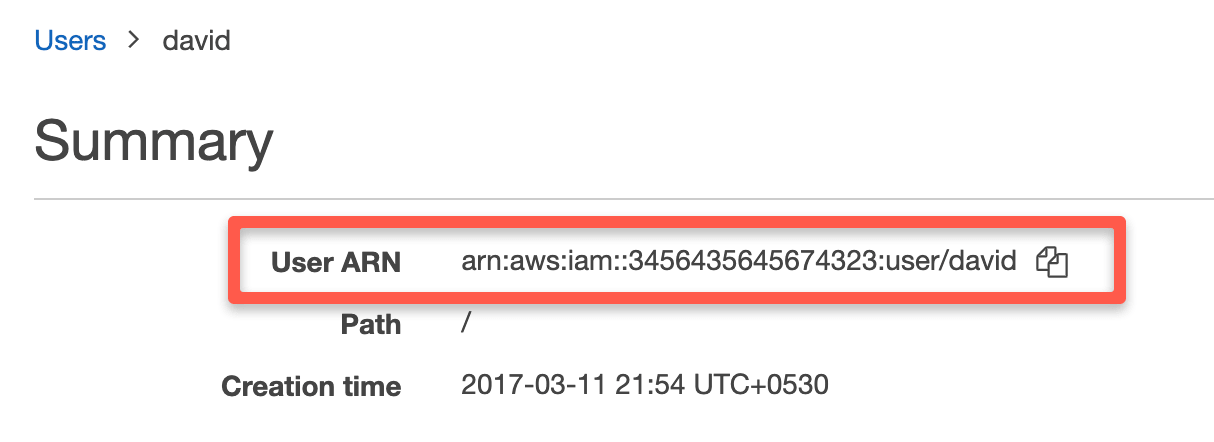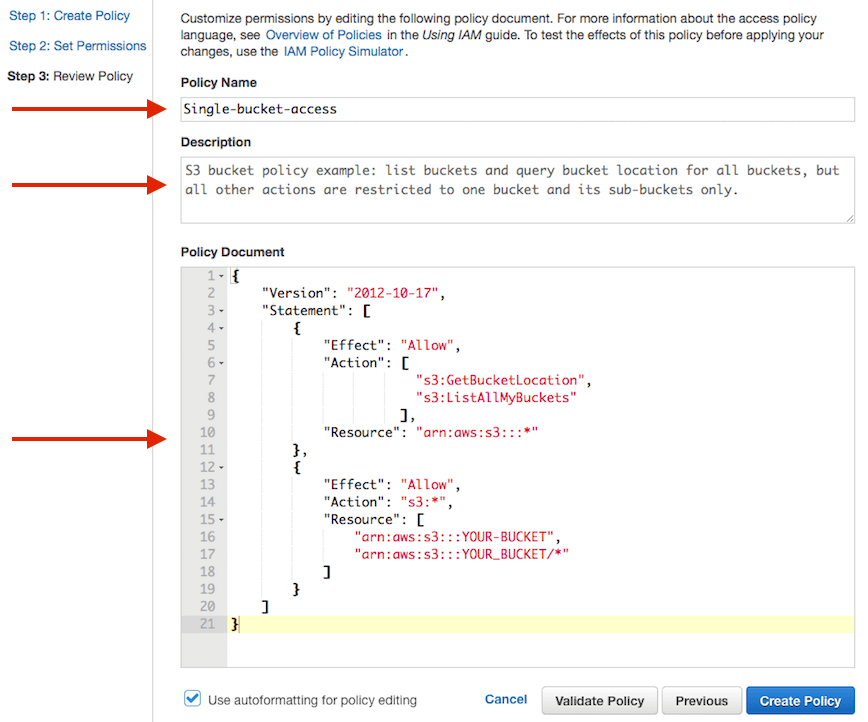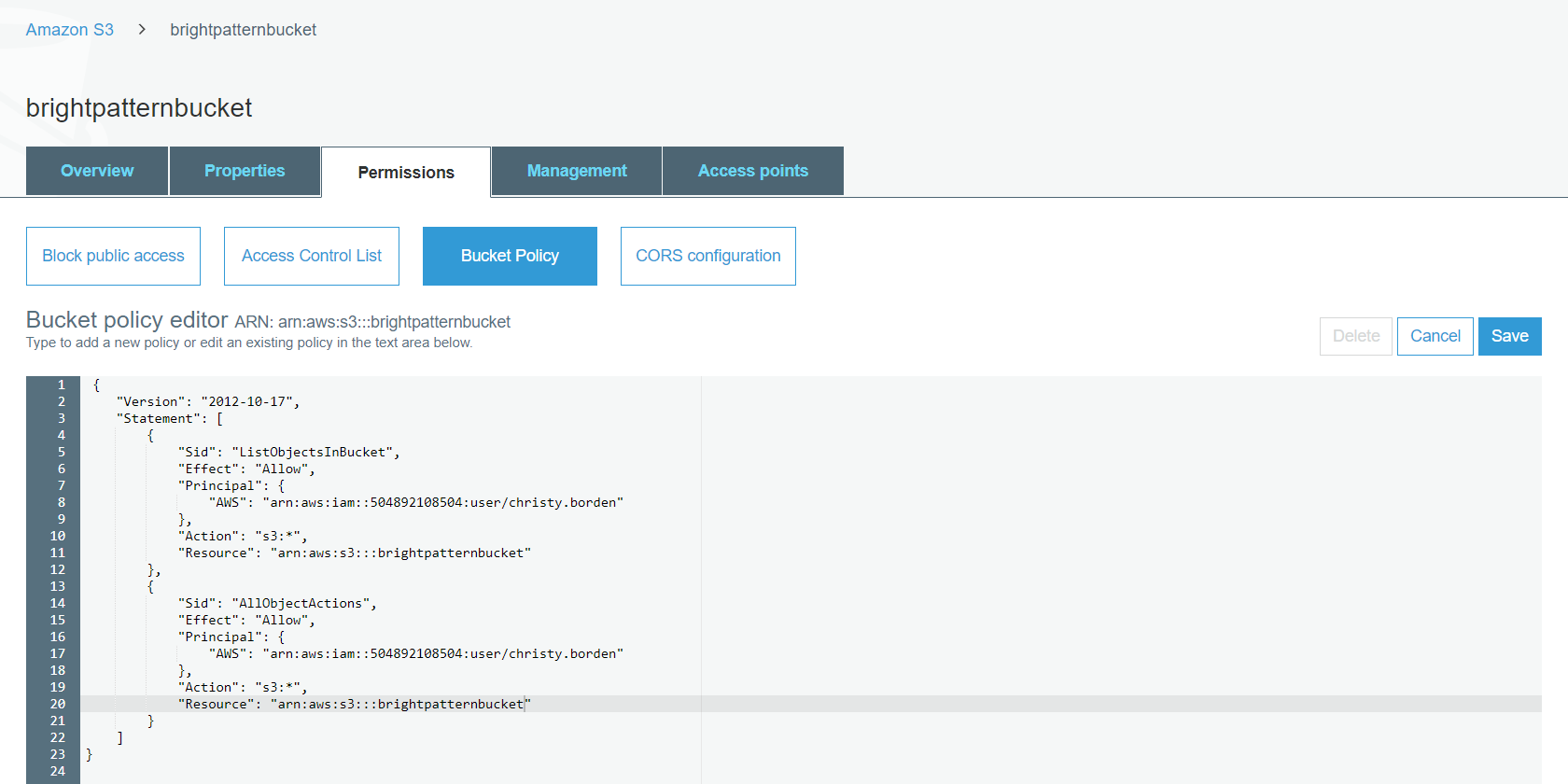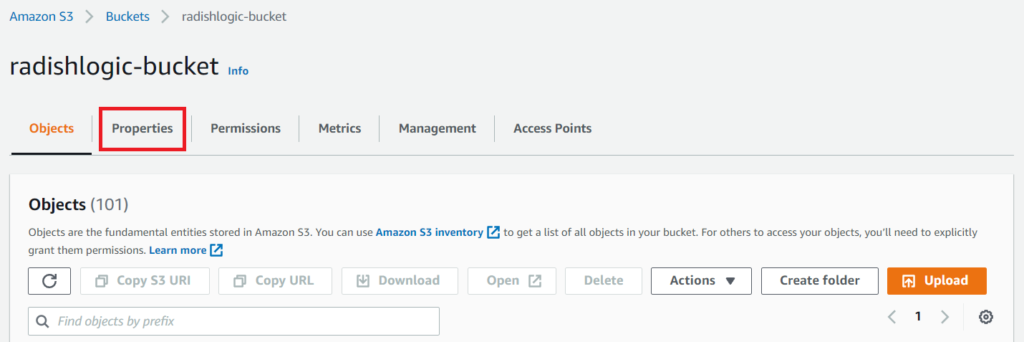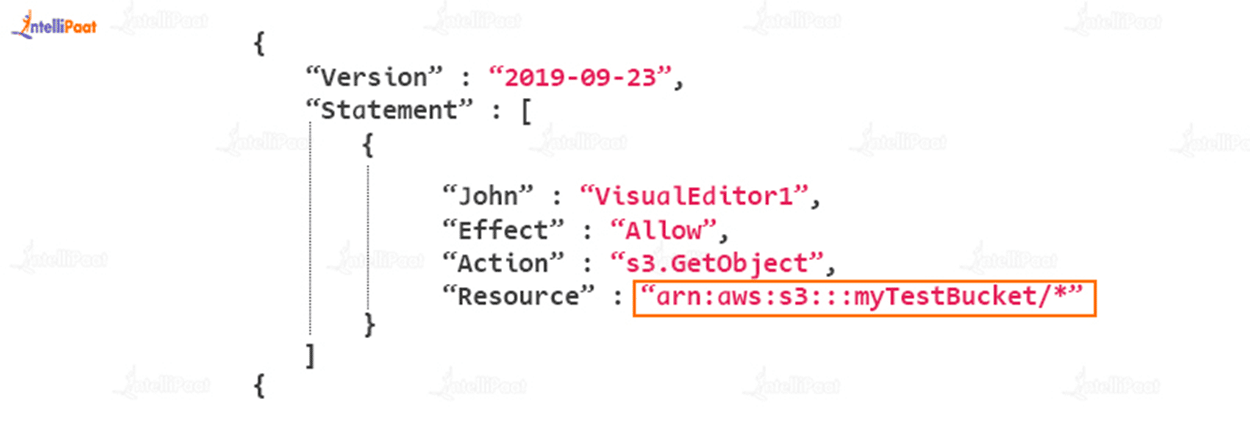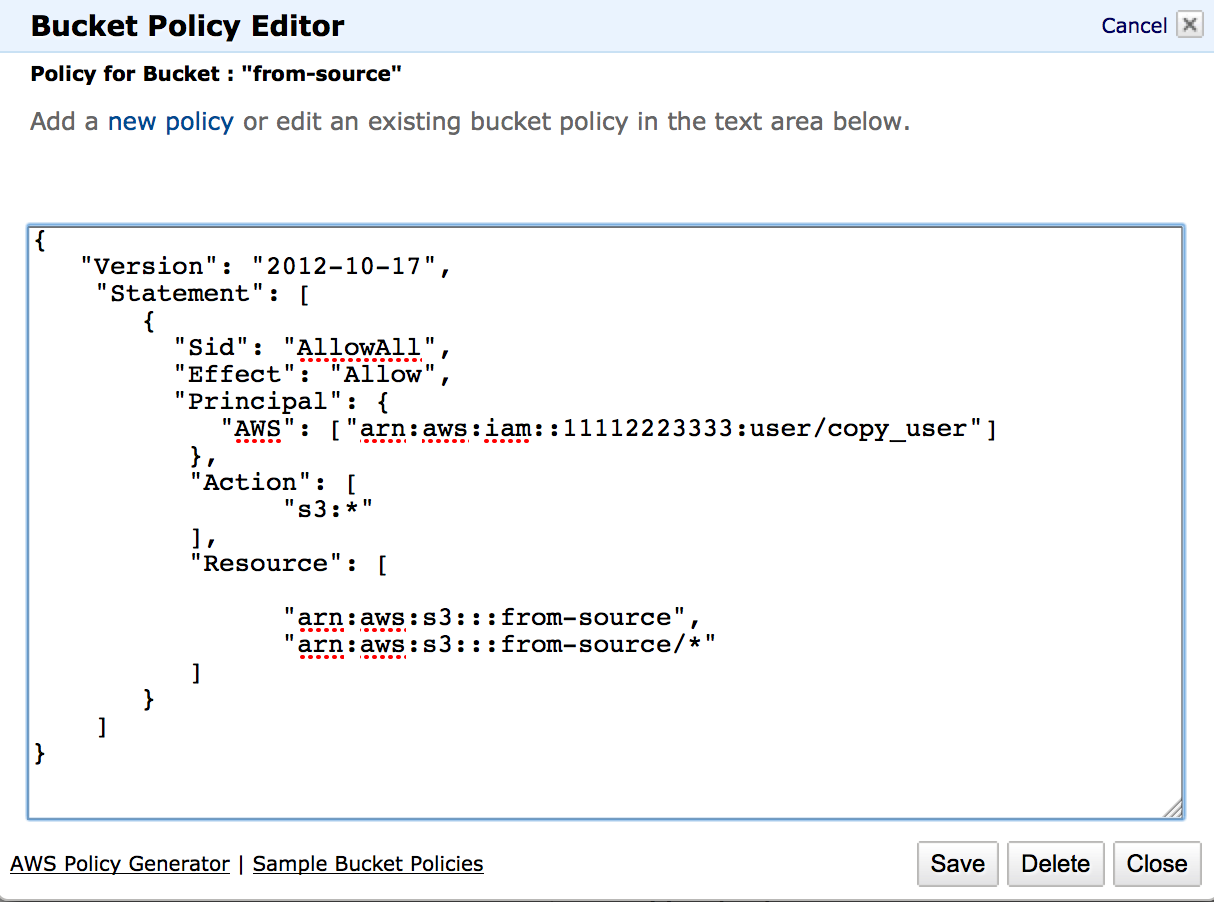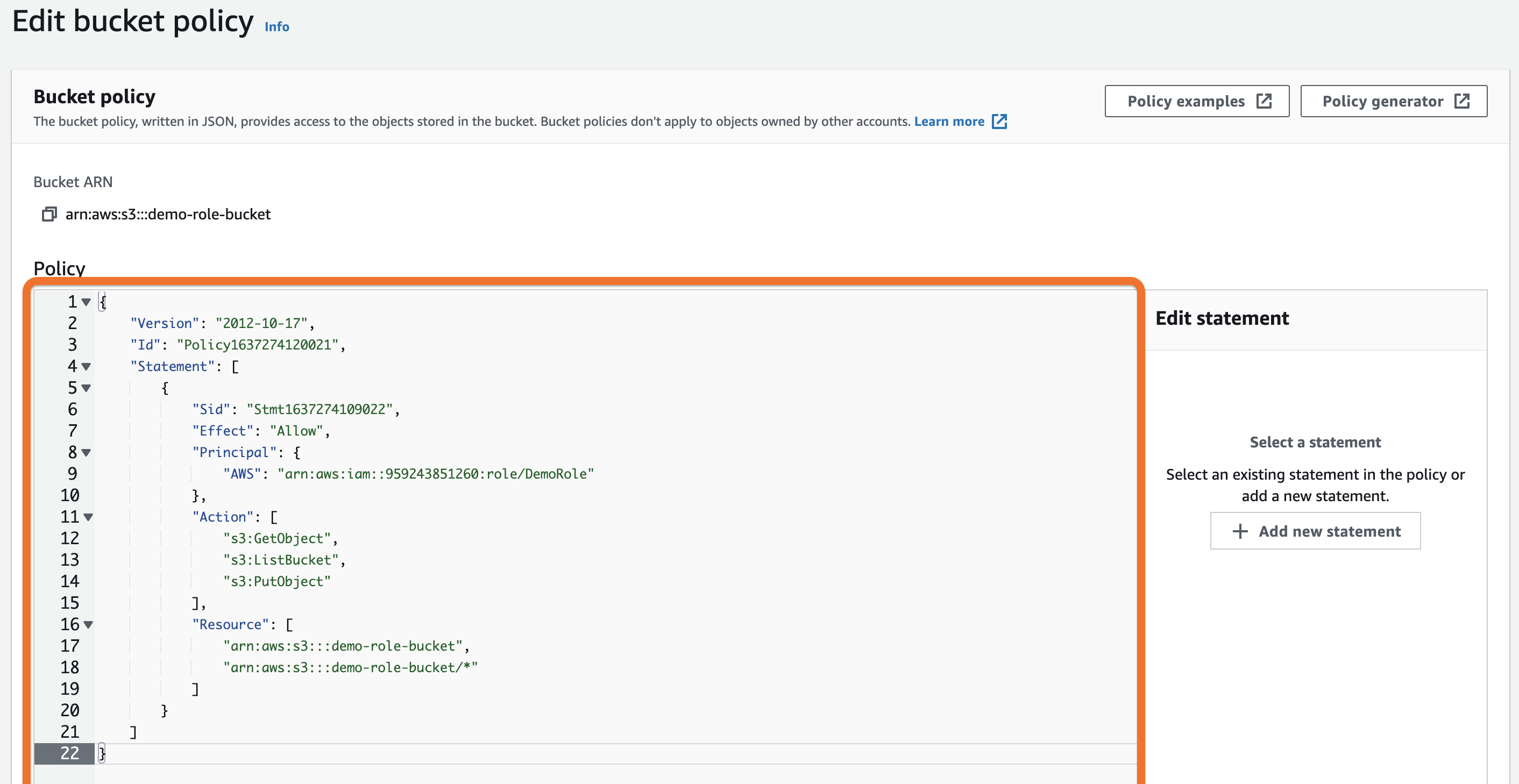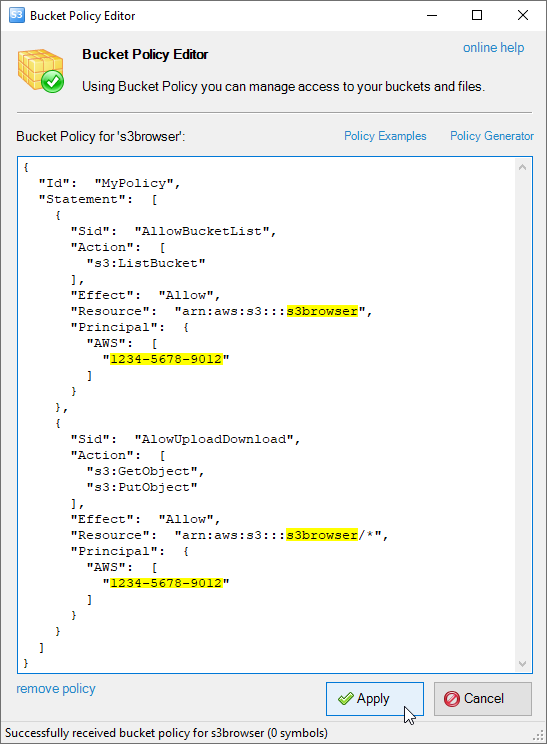
Bucket Sharing Tutorial. How to share Amazon S3 Bucket with another AWS Account. How to grant access to your bucket.

Validate access to your S3 buckets before deploying permissions changes with IAM Access Analyzer | AWS Security Blog

Validate access to your S3 buckets before deploying permissions changes with IAM Access Analyzer | AWS Security Blog

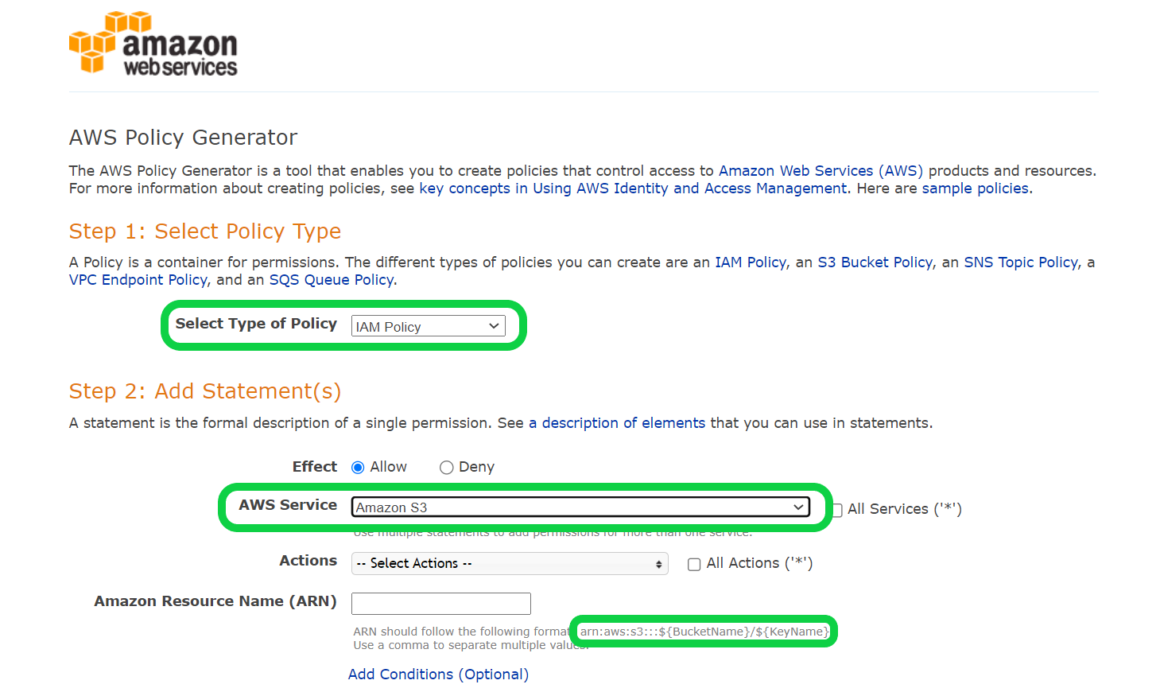
amazon web services - AWS Policy Generator giving error with S3 ARN: "Resource field is not valid. You must enter a valid ARN." - Stack Overflow